...
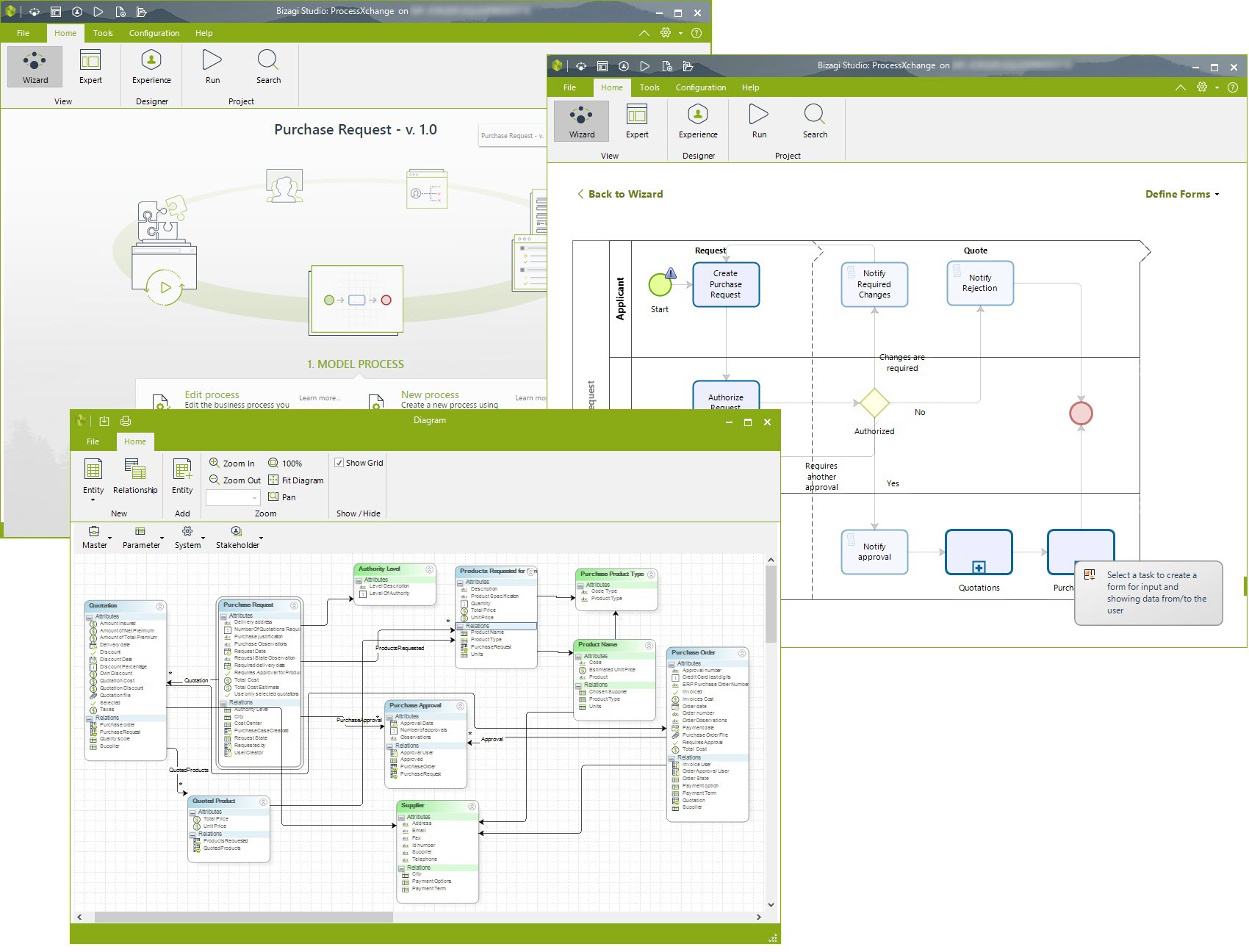
Bizagi Studio
Bizagi Studio transforms your process models into running applications, enabling you to distribute them across your organization at lightning speed. No coding, no hassle—just a simple web application that allows you to adapt your processes to an ever-changing world.
With Bizagi Studio, continuous improvement becomes a reality. Welcome to enterprise software that works.
Key Features
Process IS the Application
- Turn your process into a web application and adapt it instantly.
- No coding required and fully compliant with the latest web standards.
Achieve Results Fast
- The data layer promotes reuse, allowing you to quickly and cost-effectively share business objects across processes and projects.
Code-Free Forms
- Drag and drop your attributes into any of our auto-generated forms. It’s simple and intuitive.
Flexible Business Rules
- Manage and share business policies and rules across projects.
- Make changes effortlessly and implement them instantly.
Workload Balancing and Routing
- Gain total control over resources.
- Define work allocation, optimize and balance workloads using built-in algorithms, and manage delegates and working calendars.
Easy Integration
- Connect Bizagi data with your IT assets using our powerful SOA-based engine.
- Integrate with platforms like SAP, Documentum, SharePoint, and Outlook without the need for programming.
Integrated Runtime Environment
Bizagi Studio features an integrated runtime environment where you can log in to test your automation process. During the building process, this runtime environment—called the Work Portal—reflects real-time changes made in Bizagi Studio.
FIPS-140 Compliance
Bizagi Studio adheres to the United States Federal Information Processing Standard (FIPS) for cryptographic algorithms, ensuring the protection of sensitive data for US Federal government computer systems.
Approved Algorithms
The table below shows the equivalence between unsupported algorithms and FIPS-approved algorithms:
| Not Allowed Algorithm | [FIPS] Allowed Algorithm |
|---|---|
SHA256Managed | SHA256Cng |
SHA1Managed | SHA1Cng |
SHA512Managed | SHA512Cng |
RijndaelManaged | AesCryptoServiceProvider |
MD5CryptoServiceProvider | SHA256Cng |
MD5CryptoServiceProvider | SHA1Cng |
MD5CryptoServiceProvider | SHA512Cng |